
Introduction
Here is a link to the original LinkedIn article. Welcome to the 4th and final part of my series: Pi Hole as a Cyber Security tool.
I have written in length about how to install and set up the system. DNS Sinkholes can be used as a form of security hardening: aligned to different frameworks. The Australian ‘Essential Eight’ comes to mind. They can be deployed in the Enterprise, but these articles are designed for you and I to deploy the technology in your home network.
Over the course of a month, the Pi Hole has allowed over 1.2 million DNS queries from my home network alone. Over 200 thousand queries have been blocked: these domains have been linked to domains known for tracking/telemetry, in total around 16% of traffic has consisted of domains designed to track where you and I go.
Change your browser
In addition to this to harden your network further one can deploy more secure web browsers such as Brave. It is available across most hardware and software platforms.
Out of a comparison by School of Computer Science and Statistics at Trinity College Dublin, Brave was shown to not send data ‘back home’. It was compared with Google Chrome, Mozilla Firefox, Apple Safari, Brave Browser, Microsoft Edge and Yandex.
For Brave with its default settings they did not find any use of identifiers allowing tracking of IP address over time, and no sharing of the details of web pages visited with backend servers. Chrome, Firefox and Safari all share details of web pages visited with backend servers. For all three this happens via the search autocomplete feature, which sends web addresses to backend servers in real-time as they are typed.
In Chrome a persistent identifier is sent alongside these web addresses, allowing them to be linked together. In addition, Firefox includes identifiers in its telemetry transmissions that can potentially be used to link these over time. Telemetry can be disabled, but again is silently enabled by default. Firefox also maintains an open web-socket for push notifications that is linked to a unique identifier and so potentially can also be used for tracking and which cannot be easily disabled.
Safari defaults to a choice of start page that potentially leaks information to multiple third parties and allows them to preload pages containing identifiers to the browser cache.
Safari otherwise made no extraneous network connections and transmitted no persistent identifiers, but allied iCloud processes did make connections containing identifiers.
The effect of Pi Hole on the browsing experience using different websites
Website requests reduced by an average of 400% resulting in a faster, safer browsing experience. This was tested on Google Chrome on the Mac running Monterey.
Before Pi Hole: news.com.au
622 requests, 6.1mb transferred, 12.5mb resources, Finish 21.76s

With Pi Hole: news.com.au
122 requests, 2.1mb transferred, 2.9mb resources, finish 2.6 seconds

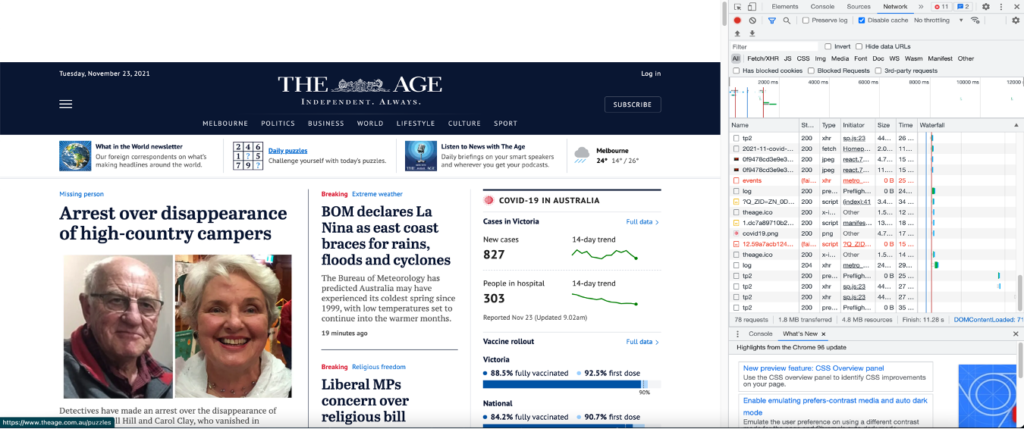
Before Pi Hole: theage.com.au
585 requests, 6.5mb transferred, 14.4mb resources, finish 31.84s

After Pi Hole: theage.com.au
78 requests, 1.8mb transferred, 4.8mb resources, finish 11.28
Before Pi Hole: theverge.com
657 requests, 10.4mb transferred, 22.1mb resources, finish 30.89s

After Pi Hole: theverge.com
53 requests, 1.3mb transferred, 2.6mb resources, finish 6.40s

As you can see, just deploying the Pi Hole to do its basic functions results in a markedly superior browsing experience. I would like to test this further in the future using older hardware (old iPads, old Android Phones). In addition I would like to install Pi Hole and Splunk on a single server running at home in combination with an open source firewall such as PfSense.
Who knows? Maybe that can form the basis of a new set of articles?
Conclusions
The lessons learned from this project are as follows:
- Browsing data is tracked.
- This traffic is a significant part of your web traffic.
- Educate yourself about the risks, manage and mitigate said risks.
- Share your knowledge with others.
- Harden your network.
Thank you for your time!